
Apple’s newest beta version of iOS 14 has a setting that will change the way people connect and stay connected to Wi-Fi networks. While other operating systems, including Android 10, already had this feature, it has much broader implications for Apple devices because the adoption rate of new iOS versions is so much higher than on Android. Also, Apple has gone a step further with iOS 14 and added automatic randomization of the MAC address every 24 hours, whereas on Android, it stays consistent for each network after joining. The way the industry has been trending, this really isn’t that surprising.
What is a MAC address?
Let’s back up a little bit. A media access control (MAC) address is a unique string of letters and numbers that is used to identify a device on a network and allow it to communicate with other devices. MAC addresses are usually assigned when the device is manufactured and, unlike IP addresses, they generally do not change when moving from one network to another. In other words, MAC addresses have historically been static and unique to each device.
How are MAC addresses used for Wi-Fi networks today?
The assumption and practice of having a static MAC address resulted in many networks leveraging it for a variety of purposes. There are well-known hospitality brands that have implemented automatic authentication programs for loyalty customers based on storing and recognizing a device’s static MAC address. In the hospitality and multifamily markets, the use of a static MAC address is far reaching in current network architectures. The notion of a dynamic MAC address changing through time by virtue of a device’s operating system will significantly alter the connectivity experience, unless they adopt solutions that plan for and address this, such as ElevenOS.
What is MAC address randomization and why is it used?
MAC address randomization is the increasing trend of device operating systems using a random, anonymous device identifier instead of the real address when connecting to wireless networks. The goal of doing this is to increase user privacy by preventing network operators from being able track devices using the real address as a consistent device identifier.
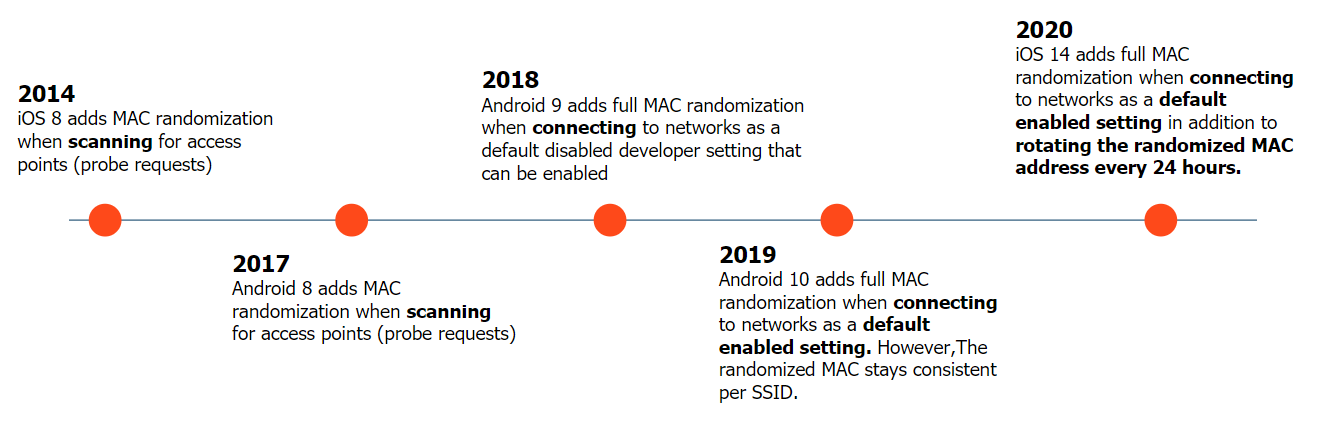
For many years now, most operating systems (iOS 8+, Android 8+, Windows 10, etc.) have implemented some form of MAC randomization. However, most of these operating systems only use a randomized MAC address when scanning for access points and SSIDs (known as probe requests), but still have used a consistent, genuine MAC address when actually connecting to networks. This has successfully mitigated some forms of tracking (footfall tracking in retail stores for example), but more advanced tracking methods have surfaced since these changes were introduced. In late 2019, Google released Android 10 which made MAC randomization the default behavior when both scanning for wireless networks and connecting to them. This was a major change that was intended to prevent tracking across networks.
Historically, MAC addresses have been a reliable identifier. However, as we learn more about privacy and security, we now know that spoofing other people's MAC addresses has been a serious network vulnerability on visitor-based Wi-Fi for some time. These changes by handset manufacturers are going to force everyone to fix this, which is ultimately a really good thing for everyone.
What is changing with iOS 14 on Apple devices?
In the latest beta version of iOS 14, Apple implemented their own improved version of MAC randomization for devices running iOS. Similar to Android 10, iOS 14 devices will use a randomized MAC address by default when both scanning and connecting to most wireless networks. Additionally, iOS has added an extra layer of privacy protection: devices with the randomization feature turned on will rotate their MAC address every 24 hours after connecting to a wireless network. This means that, by default, when an Apple device running iOS14 connects to a new network, the network will never be aware of the real, genuine MAC address of the device, but only an anonymous, temporary identifier that changes every day. There are variations to this behavior that we have been testing in lab environments. For example, migrating an existing device from iOS 13 to iOS 14 results in previously remembered WPA2 networks NOT being set to randomized. The new system default applies primarily to new networks going forward.
This “Private MAC Address” feature is network-specific and will be enabled by default on most new wireless networks that users join after they update to iOS 14. When enabled, this feature will randomize the MAC address that is used when connecting to a wireless network for the first time, randomize it every 24 hours after the user has connected, and randomize it immediately if the user forgets the network and rejoins. iOS 14 will not randomize the MAC address if the user is mid-session and actively passing traffic, even if it has been 24 hours since joining the network.
Many networks currently rely on the MAC address as a consistent identifier for the duration of the visitor’s stay at the venue. Some networks rely on the MAC address to be consistent across Wi-Fi venues as well, which previously allowed their visitors to roam between multiple venues and be automatically authenticated. This experience will not be possible for users of iOS 14 with the Private MAC Address feature enabled.
It’s important to note that just because the Private MAC Address feature is enabled by default in Beta 1 of iOS14, that doesn’t necessarily mean it will be this way in the general release. It is also worth noting that past adoption of Apple’s latest iOS has been relatively high. For example over 77% of Apple devices introduced in the last four years (estimated at 1 billion) are running some version of iOS 13, which was first released in Q4 of 2019. If iOS 14 sees similar adoption rates, there could be hundreds of millions of users impacted by this change within months of its release.
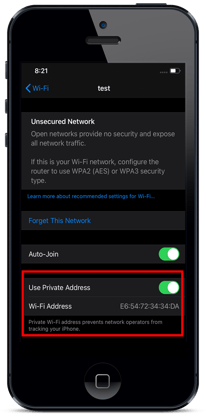
Toggling “Use Private Address” is the switch that effectively turns on and off MAC Address Randomization (here called “Wi-Fi Address”). Toggled “On” the MAC Address is changed by the device’s OS every twenty four hours. This setting is network specific. In other words, more sophisticated users can and likely will turn it on for some networks and off for others. The default setting in the Beta Version of iOS 14 has it enabled for most ALL newly added networks. That is significant. The issue would be far smaller if this setting was present, but not enabled by default. It is the default nature of this new capability that makes it broadly impactful to all iOS 14 users.
Instructing users to disable the “Use Private Address” setting has the additional challenge in that it could be perceived as compromising the user’s privacy. The iOS 14 screen says, “Private Wi-Fi address prevents network operators from tracking your iPhone.” Instructing users to disable this feature could be misconstrued as the operator’s intent to track users, even when the intent might just be to allow users to stay automatically connected to the network rather than having to manually connect via the captive portal page each day.
What does this all mean for Wi-Fi experience?
Users with these devices (Apple iPhones running iOS 14 and Apple iPads running iPadOS 14) who have the setting enabled will be forced to reconnect their device via a captive portal every 24 hours. Some users may even be forced to reconnect more often than that if they are leaving and coming back to the Wi-Fi venue. Having to reconnect devices can be a minor inconvenience or a huge pain depending on the use case.
The increasingly dynamic nature of the MAC Address is one of the reasons we developed our Hotspot 2.0 solution and have been strong proponents of it for years. Hotspot 2.0 does not rely on a MAC address for authentication, rather it is a certificate based approach to identifying and automatically authenticating a device onto a network. Hotspot 2.0 authentication is a great option for brands that value loyalty, like hospitality and retail, check out our blog post, How Hotspot 2.0 Streamlines Guest Wi-Fi Access, to learn more. In industries like multifamily, we believe the future is our Personal Pass Key solution, which does not rely on a portal or MAC address for authentication.
Subscribe to our blog to get the next installment of this post where we discuss best practices for how best to manage the upcoming proliferation of MAC address randomization.